Vulnerabilities in a system create risks; risk management is about avoiding, transferring or assuming these risks. Risk management must also take the context of where the system is being used for example a one hundred thousand dollar security system is useless in a home network since a home network would not cost anywhere near that figure. If too little control is implemented to reduce risk then the system will become insecure and have a high risk of being attacked. If too much security is implemented then system functionality and usability will reduce. Risk management becomes a three way see-saw balance, if just one security element is focused on then the system will lack in one or both of the other elements but if a balance of all three elements are used then the system can become a secure, functional and easy to use. To reduce potential threats security software is installed on machines. Since all computer systems setups are different the defaults that virus and firewall programs have are simply not enough for effective security. Users must protect themselves, a virus and firewall program my have all the needed functionalities of setting up a secure computer. A recent survey but the American Online and National Cyber Security Alliance found that out of 329 homes 67% either had no anti-virus software on their system at all or had not updated it within the previous week. These statistics show that knowledge of how to protect your computer from malware is poor. Consequently if user can find, understand and use the security features imbedded in the software by having good usability the user will utilize the full functionality of the software and create a secure system.
Focusing heavily on a secure system reduces the functionality and usability of the system. For example having a complete firewall block of incoming and outgoing data makes the system very secure since no harmful data can get in. The firewall cuts of any internet of network connections that the computer might have had. The functionality of the network and internet connection still exists but because of the firewall block the usability of the network is non existent. Therefore if there is a heavy focus on the security of a system poor usability is created and through poor usability the functionality of the computer is drastically reduced as the user can only perform offline tasks this can be seen on the graph below.
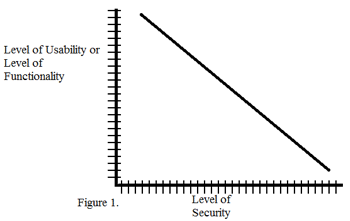
Level of Security versus Usability or functionality
Figure 1 illustrates the negative correlation between: Usability and Security or Functionality and Security. Either the system has high functionality or usability but runs a risk of being attacked. The figure illustrates the trade off between the two sets of variables a high level of security will create a lower level of usability or functionality.
Focusing heavily on a functional and usable system can lead to a decrease in the security of the system. It could be argued that a functional and usable system would be a system which has no virus software or firewall at all and ignore the risk of an attack. Initially this could be a valid argument but after virus’ and other malware have made there way on to the system usability and the functionality of the system would slowly disintegrate. An intermediate spot needs to be found were the user is happy with the functionality and usability of the system but is not compromising on security.